4 FAQs about W-2 business email compromise attacks during tax season
Has your business been a victim of tax season cyber attacks? The most popular time of the year for W-2 related cyber attacks is during tax season. Read this blog post to learn more.
The most likely cyber attack a company will face will come in the form of an email. One of the most common forms of email attack is the business email compromise (BEC), and the most popular time of the year for the W-2 version of BEC is right now — tax season.
A BEC attack involves attackers sending emails disguised as coming from high-level executives within a company, such as the CEO, to lower level personnel. During tax season, the spoof email will often request that W-2s for employees be provided by return email.
While the email looks identical to the executive’s email, it is coming from — and then returned to — the criminal, not the executive, along with the W-2s and the personal information associated with the documents.
If an employee falls for the scam, the company now has experienced a serious data breach and must comply with certain legal requirements. Worse yet, the company’s employees’ sensitive personal information has been given to the attackers and they have this problem to worry about instead of performing their job. The disruption is substantial in their personal lives and for the company’s operations.
How do attackers use W-2 information?
In most cases, once the attackers have that W-2 information, they use it to attempt to file fraudulent tax returns for those employees and have their tax refunds sent to them instead of the employee. They also use it for traditional identity theft.
The attackers act very quickly once the information is obtained. In some cases, they have begun to fraudulently use the information on the same day they obtained the W-2 information from the company. Time is truly of the essence in responding to these attacks and legal assistance is necessary for properly responding to these data breach events.
Why do so many attacks happen during tax season?
Law enforcement officers and cybersecurity professionals report a drastic increase in these types of attacks during the beginning of each year because of tax season. This is consistent with what is seen in helping companies with these cases in past years, as well. The reason this type of attack is so common during tax season is because of the tax-related fraud aspect of this type of attack. That is, the attackers monetize their attacks by using the fraudulently obtained information to file fraudulent tax returns and obtain refunds from innocent victims.
And the sooner they can do this, the better their chances are of getting the refund before the taxpayer files and receives their tax refund.
If a company has not yet been targeted, it is likely that it will be very soon so it is important to be prepared.
What can you do to protect your company?
Educating employees is critical because they will be the ones who receive the emails from the attackers.
- Make them aware of this issue by sharing the information in this article with them so that they understand the threat, how it works and how it could affect them personally.
- Train them by having appropriate personnel discuss this threat with them and help them understand that they should be very suspicious of any requests to email out anything of this nature (or make payments, such as with the very similar wire transfer version of the BEC).
Have appropriate internal controls in place to protect against these types of attacks. These controls can include:
- Limit who has access to your company’s W-2s and other sensitive information as well as who has the authority to submit or approve wire payments.
- Have established procedures in place for sending W-2 information or other sensitive information as well as for submitting or approving wire payments so that dual approvals are required for these activities.
- Require employees to use an alternative means of confirming the identity of the person making the request. If the request is by email, the employee should talk to the requestor in-person or call and speak to the requestor using a known telephone number to get verbal confirmation. If the request is by telephone or fax (many times they are), then use email to confirm by using an email address known to be correct to confirm with the purported requestor. Never reply to one of these emails or call using a telephone number that is provided in one of these emails, faxes, or telephone calls.
What to do if your company is hit by an attack
- Immediately contact experienced legal counsel who understands how to guide a company through these incidents and, ideally, has appropriate contacts with law enforcement and the IRS to assist in reporting this incident quickly.
- Report the incident to the FBI or Secret Service and appropriate IRS investigators so that the IRS can implement appropriate procedures to protect the employees whose information was exposed in the W-2s.
- Prepare appropriate notifications to the people whose information was exposed and comply with all legal and regulatory reporting requirements. This should be a part of an existing incident response plan. Companies should have such a procedure in place to be better prepared if and when a security breach occurs.
- Inform employees that the IRS will never contact them directly, for the first time, via email, telephone, text message, social media or any way other than through a written “snail mail” letter.
SOURCE: Tuma, S. (19 February 2019) "4 FAQs about W-2 business email compromise attacks during tax season" (Web Blog Post). Retrieved from https://www.benefitspro.com/2019/02/19/4-faqs-about-w-2-business-email-compromise-attacks-during-tax-season/
Don’t Forget to Post OSHA Injury and Illness Data at Your Worksite
Employers who are covered by the Occupational Safety and Health Administration's (OSHA's) record-keeping rule must post a summary of 2018 work-related injury and illnesses in a noticeable place from Feb. 1 to April 30. Read this blog post from SHRM to learn more.
Employers that are covered by the Occupational Safety and Health Administration's (OSHA's) record-keeping rule must post a summary of 2018 work-related injury and illnesses in a noticeable place from Feb. 1 to April 30. Here are some compliance tips for employers to review.
Required Posting
Many employers with more than 10 employees—except for those in certain low-risk industries—must keep a record of serious work-related injuries and illnesses. But minor injuries that are treated only by first aid do not need to be recorded.
Employers must complete an incident report (Form 301) for each injury or illness and log work-related incidents on OSHA Form 300. Form 300A is a summary of the information in the log that must be posted in the worksite from Feb. 1 to April 30 each year.
"This information helps employers, workers and OSHA evaluate the safety of a workplace, understand industry hazards, and implement worker protections to reduce and eliminate hazards," according to OSHA's website.
Employers should note that they are required to keep a separate 300 log for each "establishment," which is defined as "a single physical location where business is conducted or where services or industrial operations are performed."
If employees don't work at a single physical location, then the establishment is the location from which the employees are supervised or that serves as their base.
Employers frequently ask if they need to complete and post Form 300A if there were no injuries at the relevant establishment. "The short answer is yes, " said Tressi Cordaro, an attorney with Jackson Lewis in Washington, D.C. "If an employer recorded no injuries or illnesses in 2018 for that establishment, then the employer must enter 'zero' on the total line."
Correct Signature
Before the OSHA Form 300A is posted in the worksite, a company executive must review it and certify that "he or she has examined the OSHA 300 Log and that he or she reasonably believes, based on his or her knowledge of the process by which the information was recorded, that the annual summary is correct and complete," according to OSHA.
A common mistake seen on 300A forms is that companies forget to have them signed, noted John Martin, an attorney with Ogletree Deakins in Washington, D.C.
There are only four company representatives who may certify the summary:
- An owner of the company.
- An officer of the corporation.
- The highest-ranking company official working at the site.
- The immediate supervisor of the highest-ranking company official working at the site.
Businesses commonly make the mistake of having an HR or safety supervisor sign the form, said Edwin Foulke Jr., an attorney with Fisher Phillips in Atlanta and Washington, D.C., and the former head of OSHA under President George W. Bush.
They need to get at least the plant manager to sign it, he said, noting that the representative who signs Form 300A must know how numbers in the summary were obtained.
Once the 300A form is completed, it should be posted in a conspicuous place where other employment notices are usually posted.
Electronic Filing
The Improve Tracking of Workplace Injuries and Illnesses rule requires covered establishments with at least 20 employees to also electronically submit Form 300A to OSHA.
Large establishments with 250 or more employees were also supposed to begin electronically submitting data from the 300 and 301 forms in 2018, but the federal government recently eliminated that requirement. However, those establishments still must electronically submit their 300A summaries.
The deadline to electronically submit 2018 information is March 2.
SOURCE: Nagele-Piazza, L. (1 February 2019) "Don’t Forget to Post OSHA Injury and Illness Data at Your Worksite" (Web Blog Post). Retrieved from https://www.shrm.org/resourcesandtools/legal-and-compliance/employment-law/pages/don%E2%80%99t-forget-to-post-osha-injury-and-illness-data-at-your-worksite.aspx/
OSHA Proposes Change to Electronic Record-Keeping Rule
On July 30, OSHA submitted a Notice of Proposed Rulemaking that would eliminate the requirement for worksites with 250 or more employees to electronically submit certain data. Continue reading to learn more.
Worksites with 250 or more employees would not be required to electronically submit certain data to the Occupational Safety and Health Administration (OSHA) under a proposal to roll back an Obama-era rule.
The Improve Tracking of Workplace Injuries and Illnesses rule requires employers that are covered by OSHA's record-keeping regulations to electronically submit certain reports to the federal government. Certain establishments with 20-249 employees are required to submit only OSHA Form 300A each year—300A is a summary of workplace injuries and illnesses that many employers are required to post in the workplace from Feb. 1 until April 30 of each year.
In addition to Form 300A, larger establishments (those with 250 or more employees) were supposed to begin submitting data from Form 300 (the injury and illness log) and Form 301 (incident reports for each injury or illness) in July. However, in May, OSHA announced that it would not be accepting that information in light of anticipated changes to the rule.
As expected, on July 30, OSHA issued a Notice of Proposed Rulemaking (NPRM) to eliminate the requirement for large establishments to electronically submit information from Forms 300 and 301.
"OSHA has provisionally determined that electronic submission of Forms 300 and 301 adds uncertain enforcement benefits, while significantly increasing the risk to worker privacy, considering that those forms, if collected by OSHA, could be found disclosable" under the Freedom of Information Act, the agency said.
The electronic record-keeping rule has faced considerable opposition from the business community, in part because some of the data submitted will be made available to the public.
The proposed rule would also require employers to submit their employer identification numbers (EINs) when e-filing Form 300A. "Collecting EINs would increase the likelihood that the Bureau of Labor Statistics would be able to match data collected by OSHA under the electronic reporting requirements to data collected by BLS for the Survey of Occupational Injury and Illness," the agency said.
Anti-Retaliation Rules Remain
OSHA's electronic record-keeping rule also contains controversial anti-retaliation provisions. These provisions, which went into effect in December 2016, give OSHA broad discretion to cite employers for having policies or practices that could discourage employees from reporting workplace injuries and illnesses. For example, the provisions place limitations on safety incentive programs and drug-testing policies. OSHA has said that employers should limit post-accident drug tests to situations where drug use likely contributed to the incident and for which a drug test can accurately show impairment caused by drug use.
Prior to the new rules, many employers administered post-accident drug tests to all workers who were involved in an incident. The anti-retaliation provisions create another layer of ambiguity for employers, because they have to justify why they tested one person and not another, which may lead to race, gender and other discrimination claims, said Mark Kittaka, an attorney with Barnes & Thornburg in Fort Wayne, Ind., and Columbus, Ohio.
OSHA has not announced any plans to revise the electronic record-keeping rule any further. Many employer-side stakeholders were disappointed that OSHA made no effort to revise the anti-retaliation provisions, said John Martin, an attorney with Ogletree Deakins in Washington, D.C.
There are still undecided lawsuits in federal courts that challenged these provisions back when they were first issued but have been put on hold while revisions were pending, Martin noted. OSHA's proposed revision clearly did not resolve all of the challengers' concerns, so they are now deciding whether to ask the courts to resume litigation, he said.
What Now?
Employers should keep in mind that OSHA's electronic record-keeping rule refers to "establishment" size, not overall employer size, Kittaka said. An establishment is a single physical location where business is conducted or where services or industrial operations are performed, according to OSHA.
Large employers still need to electronically submit 300A summaries for each work establishment—office, plant, facility, yard, etc.—with 250 or more employees, Martin said. If they have work establishments with 20-249 employees and they are covered by OSHA's high-hazard establishment list, then they must also submit 300A summaries for those smaller establishments.
The proposed rule is open for public comment until Sept. 28. "OSHA made clear in the proposed rule that the agency was only seeking comments on the electronic submission and EIN" proposals, said Tressi Cordaro, an attorney with Jackson Lewis in Washington, D.C.
SOURCE: Nagele-Piazza, L (14 August 2018) "OSHA Proposes Change to Electronic Record-Keeping Rule" (Web Blog Post). Retrieved from https://www.shrm.org/resourcesandtools/legal-and-compliance/employment-law/pages/osha-proposes-change-to-electronic-record-keeping-rule.aspx/
CenterStage: February is American Heart Month - Are Your Loved Ones Knowledgeable?
Heart disease is the leading cause of death for men and women in the United States. Every year, 1 in 4 deaths are caused by heart disease, according to the American Heart Association.
Talking with your loved ones about heart disease can be awkward, but it’s important. In fact, it could save a life. At the dinner table, in the car, or even via text, have a heart-to-heart with your loved ones about improving heart health as a family. Engaging those you care about in conversations about heart disease prevention can result in heart-healthy behavior changes.

Here are three reasons to talk to the people in your life about heart health and three ways to get the conversation started.
Three Reasons You Should Talk to Your Loved Ones About Heart Health
#1. More than physical health is at risk

Millions of people in the US don’t know that they have high blood pressure. High blood pressure raises the risk for heart attacks, stroke, heart disease, kidney disease and many other health issues. Researchers are learning that having high blood pressure in your late 40s or early 50s can lead to dementia later in life. Encourage family members to be aware of blood pressure levels and monitor them consistently.
#2. Feel Younger Longer

Just as bad living habits can age you prematurely and shorten your lifespan, practicing good heart healthy habits can help you feel younger longer. On average, U.S. adults have hearts that are 7 years older than they should be, according to the Center for Disease Control and Prevention. Just beginning the conversation with the people in your life that you care about can begin to make changes in their heart health.
#3. You Are What You Eat

Even small changes can make a big difference. Prepare healthier versions of your favorite family recipes by making simple ingredient swaps, simply searching the internet is all it usually takes to find an easy ingredient alternative. Find a new
recipe to cook for your family members, or get in the kitchen together and you’ll finish with something delicious and possibly making some new favorite memories as well. When grocery shopping, choose items low in sodium, added sugar, and trans fats, and be sure to stock up on fresh fruits and vegetables.
Three Ways to Start the Conversation
- Encourage family members to make small changes, like using spices to season food instead of salt.
- Motivate your loved ones to incorporate physical activity into every day. Consider a family fitness challenge and compete with each other to see who can achieve the best results.
- Avoid bad habits together. It has been found that smokers are twice as likely to quit if they have a support system. This applies to practicing healthier practices as well. Set goals and start by making small, positive changes, chances are they may have a big difference.
The key to heart health is a healthy lifestyle. It’s important to try to let go of bad habits that increase your risk of heart disease. By setting small, achievable goals and tracking those goals, you can possibly extend your life expectancy a little bit each day.
Heart disease can be prevented by making healthy choices and consciously monitoring health conditions. Making healthy choices a topic of conversation with your family and loved ones is a great way to open the door to healthier practices in all walks of life.
Download the PDF
SaveSaveSaveSaveSaveSave
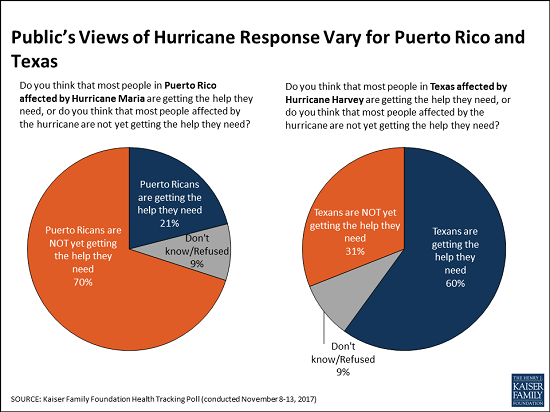
Two Months After Hurricane Maria, A Growing Majority Of Americans Say Puerto Ricans are Not Yet Getting the Help They Need
Two months after Hurricane Maria struck Puerto Rico, a growing majority of Americans say that Puerto Ricans affected by the devastating storm are not yet getting the help they need, the November Kaiser Family Foundation Tracking Poll finds.
This month, 70 percent of the public say that people in Puerto Rico are not yet getting the help they need, up from 62 percent in October 2017. These perceptions vary by party, and half of Republicans (52%) now say Puerto Ricans aren’t yet getting needed help, up significantly from October (38%).
When asked whether the federal government is doing enough to restore electricity and access to food and water in Puerto Rico or not, a majority of the public (59%) says the federal government is not doing enough, up from 52 percent in October. Most Democrats (86%) and independents (59%) say the federal government is not doing enough, but most Republicans (63%) say it is doing enough.
In contrast, Americans see the recovery efforts in Texas following Hurricane Harvey in late August progressing more positively. Most (60%) of the public says Texans are getting the help they need, twice the share (31%) who say Texans aren’t yet getting needed help.
The poll finds similar shares of Americans they are closely following news about recovery efforts in Puerto Rico (63%) and in Texas (58%). Democrats are somewhat more likely to report closely following news about the Puerto Rico recovery (75%) than are independents (61%) and Republicans (54%). In contrast, there are no partisan differences for those following news about Texas.
Designed and analyzed by public opinion researchers at the Kaiser Family Foundation, the poll was conducted from November 8 – 13, 2017 among a nationally representative random digit dial telephone sample of 1,201 adults. Interviews were conducted in English and Spanish by landline (415) and cell phone (786). The margin of sampling error is plus or minus 3 percentage points for the full sample. For results based on subgroups, the margin of sampling error may be higher.
You can read the original article here.
Source:
Kaiser Family Foundation (20 November 2017). "Two Months After Hurricane Maria, A Growing Majority Of Americans Say Puerto Ricans are Not Yet Getting the Help They Need" [Web blog post]. Retrieved from address https://www.kff.org/other/press-release/poll-two-months-after-hurricane-maria-a-growing-majority-of-americans-say-puerto-ricans-are-not-ye-getting-the-help-they-need/
SaveSave
Taking A Page From Pharma’s Playbook To Fight The Opioid Crisis
From Kaiser Health News, here is the latest: an interview with Dr. Mary Meengs, medical director at the Humboldt Independent Practice Association, on curbing opioid addiction through the reduction of prescription painkillers.
Dr. Mary Meengs remembers the days, a couple of decades ago, when pharmaceutical salespeople would drop into her family practice in Chicago, eager to catch a moment between patients so they could pitch her a new drug.
Now living in Humboldt County, Calif., Meengs is taking a page from the pharmaceutical industry’s playbook with an opposite goal in mind: to reduce the use of prescription painkillers.
Meengs, medical director at the Humboldt Independent Practice Association, is one of 10 California doctors and pharmacists funded by Obama-era federal grants to persuade medical colleagues in Northern California to help curb opioid addiction by altering their prescribing habits.
She committed this past summer to a two-year project consisting of occasional visits to medical providers in California’s most rural areas, where opioid deaths and prescribing rates are high.
“I view it as peer education,” Meengs said. “They don’t have to attend a lecture half an hour away. I’m doing it at [their] convenience.”
This one-on-one, personalized medical education is called “academic detailing” — lifted from the term “pharmaceutical detailing” used by industry salespeople.
Detailing is “like fighting fire with fire,” said Dr. Jerry Avorn, a Harvard Medical School professor who helped develop the concept 38 years ago. “There is some poetic justice in the fact that these programs are using the same kind of marketing approach to disseminate helpful evidence-based information as some [drug] companies were using … to disseminate less helpful and occasionally distorted information.”
Recent lawsuits have alleged that drug companies pushed painkillers too aggressively, laying the groundwork for widespread opioid addiction.
Avorn noted that detailing has also been used to persuade doctors to cut back on unnecessary antibiotics and to discourage the use of expensive Alzheimer’s disease medications that have side effects.
Kaiser Permanente, a large medical system that operates in California, as well as seven other states and Washington, D.C., has used the approach to change the opioid-prescribing methods of its doctors since at least 2013. (Kaiser Health News is not affiliated with Kaiser Permanente.)
In California, detailing is just one of the ways in which state health officials are attempting to curtail opioid addiction. The state is also expanding access to medication-assisted addiction treatment under a different, $90 million grant through the federal 21st Century Cures Act.
The total budget for the detailing project in California is less than $2 million. The state’s Department of Public Health oversees it, but the money comes from the federal Centers for Disease Control and Prevention through a program called “Prevention for States,” which provides funding for 29 states to help combat prescription drug overdoses.
The California doctors and pharmacists who conduct the detailing conversations are focusing on their peers in the three counties hardest hit by opioid addiction: Lake, Shasta and Humboldt.
They arrive armed with binders full of facts and figures from the CDC to help inform their fellow providers about easing patients off prescription painkillers, treating addiction with medication and writing more prescriptions for naloxone, a drug that reverses the toxic effects of an overdose.
“Academic detailing is a sales pitch, an evidence-based … sales pitch,” said Dr. Phillip Coffin, director of substance-use research at San Francisco’s Department of Public Health — the agency hired by the state to train the detailers.
In an earlier effort, Coffin said, his department conducted detailing sessions with 40 San Francisco doctors, who have since increased their prescriptions of naloxone elevenfold.
“One-on-one time with the providers, even if it was just three or four minutes, was hugely beneficial,” Coffin said. He noted that the discussions usually focused on specific patients, which is “way more helpful” than talking generally about prescription practices.
Meengs and her fellow detailers hope to make a dent in the magnitude of addiction in sparsely populated Humboldt County, where the opioid death rate was the second-highest in California last year — almost five times the statewide average. Thirty-three people died of opioid overdoses in Humboldt last year.
One recent afternoon, Meengs paid a visit during the lunch hour to Fortuna Family Medical Group in Fortuna, a town of about 12,000 people in Humboldt County.
“Anybody here ever known somebody, a patient, who passed away from an overdose?” Meengs asked the group — a physician, two nurses and a physician assistant — who gathered around her in the waiting room, which they had temporarily closed to patients.
“I think we all do,” replied the physician, Dr. Ruben Brinckhaus.
Brinckhaus said about half the patients at the practice have a prescription for an opioid, anti-anxiety drug or other controlled substance. Some of them had been introduced to the drugs years ago by other prescribers.

Dr. Ruben Brinckhaus says his small family practice in Fortuna, Calif., has been trying to wean patients off opiates. (Pauline Bartolone/California Healthline)
Meengs’ main goal was to discuss ways in which the Fortuna group could wean its patients off opioids. But she was not there to scold or lecture them. She asked the providers what their challenges were, so she could help them overcome them.
Meengs will keep making office calls until August 2019 in the hope that changes in the prescribing behavior of doctors will eventually help tame the addiction crisis.
“It’s a big ship to turn around,” said Meengs. “It takes time.”
Source:
Bartolone P. (14 November 2017). "Taking A Page From Pharma’s Playbook To Fight The Opioid Crisis" [Web blog post]. Retrieved from address https://khn.org/news/taking-a-page-from-pharmas-playbook-to-fight-the-opioid-crisis/
SaveSave
Absent federal action, states take the lead on curbing drug costs
What's your state's stance on the cost of prescription drugs? See how Maryland has moved forward in their decision making for drug prices, giving themselves the ability to say "no" in this article from Benefits Pro written by Shefali Luthra.
You can read the original article here.
Lawmakers in Maryland are daring to legislate where their federal counterparts have not: As of Oct. 1, the state will be able to say “no” to some pharmaceutical price spikes.
A new law, which focuses on generic and off-patent drugs, empowers the state’s attorney general to step in if a drug’s price climbs 50 percent or more in a single year. The company must justify the hike. If the attorney general still finds the increase unwarranted, he or she can file suit in state court. Manufacturers face a fine of up to $10,000 for price gouging.
As Congress stalls on what voters say is a top health concern — high pharmaceutical costs — states increasingly are tackling the issue. Despite often-fierce industry opposition, a variety of bills are working their way through state governments. California, Nevada and New York are among those joining Maryland in passing legislation meant to undercut skyrocketing drug prices.
Maryland, though, is the first to penalize drugmakers for price hikes. Its law passed May 26 without the governor’s signature.
The state-level momentum raises the possibility that — as happened with hot-button issues such as gay marriage and smoke-free buildings — a patchwork of bills across the country could pave the way for more comprehensive national action. States feel the squeeze of these steep price tags in Medicaid and state employee benefit programs, and that applies pressure to find solutions.
“There is a noticeable uptick among state legislatures and state governments in terms of what kind of role states can play in addressing the cost of prescription drugs and access,” said Richard Cauchi, health program director at the National Conference of State Legislatures.
Many experts frame Maryland’s law as a test case that could help define what powers states have and what limits they face in doing battle with the pharmaceutical industry.
The generic-drug industry has already filed a lawsuit to block the law, arguing it’s unconstitutionally vague and an overreach of state powers. A district court is expected to rule soon.
The state-level actions focus on a variety of tactics:
“Transparency bills” would require pharmaceutical companies to detail a drug’s production and advertising costs when they raise prices over certain thresholds. Cost-limit measures would cap drug prices charged by drugmakers to Medicaid or other state-run programs, or limit what the state will pay for drugs. Supply-chain restrictions include regulating the roles of pharmacy benefit managers or limiting a consumer’s out-of-pocket costs.
A New York law on the books since spring allows officials to cap what its Medicaid program will pay for medications. If companies don’t sufficiently discount a drug, a state review will assess whether the price is out of step with medical value.
Maryland’s measure goes further — treating price gouging as a civil offense and taking alleged violators to court.
“It’s a really innovative approach. States are looking at how to replicate it, and how to expand on it,” said Ellen Albritton, a senior policy analyst at the left-leaning Families USA, which has consulted with states including Maryland on such policies.
Lawmakers have introduced similar legislation in states such as Massachusetts, Rhode Island, Tennessee and Montana. And in Ohio voters are weighing a ballot initiative in November that would limit what the state pays for prescription drugs in its Medicaid program and other state health plans.
Meanwhile, the California legislature passed a bill earlier in September that would require drugmakers to disclose when they are about to raise a price more than 16 percent over two years and justify the hike. It awaits Democratic Gov. Jerry Brown’s signature.
In June, Nevada lawmakers approved a law similar to California’s but limited to insulin prices. Vermont passed a transparency law in 2016 that would scrutinize up to 15 drugs for which the state spends “significant health care dollars” and prices had climbed by set amounts in recent years.
But states face a steep uphill climb in passing pricing legislation given the deep-pocketed pharmaceutical industry, which can finance strong opposition, whether through lobbying, legal action or advertising campaigns.
Last fall, voters rejected a California initiative that would have capped what the state pays for drugs — much like the Ohio measure under consideration. Industry groups spent more than $100 million to defeat it, putting it among California’s all-time most expensive ballot fights. Ohio’s measure is attracting similar heat, with drug companies outspending opponents about 5-to-1.
States also face policy challenges and limits to their statutory authority, which is why several have focused their efforts on specific parts of the drug-pricing pipeline.
Critics see these tailored initiatives as falling short or opening other loopholes. Requiring companies to report prices past a certain threshold, for example, might encourage them to consistently set prices just below that level.
Maryland’s law is noteworthy because it includes a fine for drugmakers if price increases are deemed excessive — though in the industry that $10,000 fine is likely nominal, suggested Rachel Sachs, an associate law professor at Washington University in St. Louis who researches drug regulations.
This law also doesn’t address the trickier policy question: a drug’s initial price tag, noted Rena Conti, an assistant professor in the University of Chicago who studies pharmaceutical economics.
And its focus on generics means that branded drugs, such as Mylan’s Epi-Pen or Kaleo’s overdose-reversing Evzio, wouldn’t be affected.
Yet there’s a good reason for this, noted Jeremy Greene, a professor of medicine and the history of medicine at Johns Hopkins University who is in favor of Maryland’s law.
Current interpretation of federal patent law suggests that the issues related to the development and affordability of on-patent drugs are under federal jurisdiction, outside the purview of states, he explained.
In Maryland, “the law was drafted narrowly to address specifically a problem we’ve only become aware of in recent years,” he said. That’s the high cost of older, off-patent drugs that face little market competition. “Here’s where the state of Maryland is trying to do something,” he said.
Still, a ruling against the state in the pending court case could have a chilling effect for other states, Sachs said, although it would be unlikely to quash their efforts.
“This is continuing to be a topic of discussion, and a problem for consumers,” said Sachs.
“At some point, some of these laws are going to go into effect — or the federal government is going to do something,” she added.
Kaiser Health News, a nonprofit health newsroom whose stories appear in news outlets nationwide, is an editorially independent part of the Kaiser Family Foundation. KHN’s coverage of prescription drug development, costs and pricing is supported in part by the Laura and John Arnold Foundation.
Source:
Luther S. (29 September 2017). "Absent federal action, states take the lead on curbing drug costs" [Web Blog Post]. Retrieved from address https://www.benefitspro.com/2017/09/29/absent-federal-action-states-take-the-lead-on-curb?page=2
4 Trends Shaping Cybersecurity in 2017
The threat of cyber attacks is increasing every day. Make sure you are stay up-to-date with all the recent news and trends happening in the world of cyber security so you can stay informed on how to protect yourself from cyber threats. Check out this great column by Denny Jacob from Property Casualty 360 and find out about the top 4 trends impacting cybersecurity this year.
No. 4: Growing areas of concern
Organizations with a chief information security officer (CISO) in 2017 increased to 65 percent compared to 50 percent in 2016. Staffing challenges and budgetary distribution, however, reveal where organizations face exposure.
Finding qualified personnel to fill cybersecurity positions is as ongoing challenge. For example, one-third of study respondents note that their enterprises receive more than 10 applicants for an open position. More than half of those applicants, however, are unqualified. Even skilled applicants require time and training before their job performance is up to par with others who are already working on the company's cybersecurity operation.
Half of the study respondents reported security budgets will increase in 2017, which is down from 65 percent of respondents who reported an increase in 2016. This, along with staffing challenges, has many enterprises reliant on both automation and external resources to offset missing skills on the cybersecurity team.
Another challenge: Relying on third-party vendors means there must be funds available to offset any personnel shortage.
If the skills gap continues unabated and the funding for automation and external third-party support is reduced, businesses will struggle to fill their cybersecurity needs.
No. 3: More complicated cyber threats
Faced with declining budgets, businesses will have less funding available on a per-attack basis. Meanwhile, the number of attacks is growing, and they are becoming more sophisticated.
More than half (53 percent) of respondents noted an increase in the overall number of attacks compared previous years. Only half (roughly 50 percent) said their companies executed a cybersecurity incident response plan in 2016.
Here are some additional findings regarding the recent uptick in cyber breaches:
• 10 percent of respondents reported experiencing a hijacking of corporate assets for botnet use;• 18 percent reported experiencing an advanced persistent threat (APT) attack; and
• 14 percent reported stolen credentials.
• Last year’s results for the three types of attacks were:
• 15 percent for botnet use;
• 25 percent for APT attacks; and
•15 percent involving stolen credentials.
Phishing (40 percent), malware (37 percent) and social engineering (29 percent) continue to top the charts in terms of the specific types of attacks, although their overall frequency of occurrence decreased: Although attacks are up overall, the number of attacks in these three categories is down.
No. 2: Mobile takes a backseat to IoT
Businesses are now more sophisticated in the mobile arena. The proof: Cyber breaches resulting from mobile devices are down. Only 13 percent of respondents cite lost mobile devices as an exploitation vector in 2016, compared to 34 percent in 2015. Encryption factors into the decrease; only 9 percent indicated that lost or stolen mobile devices were unencrypted.
IoT continues to rise as an area of concern. Three out of five (59 percent) of the 2016 respondents cite some level of concern relative to IoT, while an additional 30 percent are either "extremely concerned" or "very concerned" about this exposure.
IoT is an increasingly important element in governance, risk and cybersecurity activities. This is a challenging area for many, because traditional security efforts may not already cover the functions and devices feeding this digital trend.
No. 1: Ransomware is the new normal
The number of code attacks, including ransomware attacks, remains high: 62 percent of respondents reported their enterprises experienced a ransomware attackspecifically.
Half of the respondents believe financial gain is the biggest motivator for criminals, followed by disruption of service (45 percent) and theft of personally identifiable information (37 percent). Despite this trend, only 53 percent of respondents' companies have a formal process in place to deal with ransomware attacks.
What does that look like?
Businesses can conduct "tabletop" exercises that stage a ransomware event or discuss in advance decisions about payment vs. non-payment. Payment may seem like the easiest solution, but law enforcement agencies warn it can have an encouraging effect on those criminals as some cases lead to repeated attacks of the same business.
Many cybersecurity specialists argue that the best way to fight a ransomware attack is to avoid one in the first place. Advance planning that might include the implementation of a governing corporate policy or other operating parameters, can help to ensure that the best cybersecurity decisions are made when the time comes to battle a breach.
See the original article Here.
Source:
Jacob D. (2017 August 25). 4 trends shaping cybersecurity in 2017 [Web blog post]. Retrieved from address https://www.benefitspro.com/2017/08/25/4-trends-shaping-cybersecurity-in-2017?ref=hp-in-depth&page_all=1
The Risk of Being Uninsured (and the Hidden Bargain in Addressing It Now)
Are you aware of all the risks associated with being uninsured? Take a look at this great column by Erica Oh Nataren from Life Happens and find out how you are putting yourself in harm's way by being uninsured.
With all the expenses of everyday living, it’s tempting to think of insurance as just another cost. What’s harder to see is the potential cost of not buying insurance—or what’s known as “self-insuring”—and the hidden bargain of coverage.
The Important vs. the Urgent
We’ve all experienced it: the tendency to stay focused on putting out fires, while never getting ahead on the things that really matter in the long run. For most people, there are two big things that matter in the long run: their families and their ability to retire. And being properly insured is important to both those concerns.
Life Insurance: a Hidden Bargain?
It’s exceedingly rare, but we all know it can happen: someone’s unexpected death. Life insurance can prevent financial catastrophe for the loved ones left behind, if they depend on you for income or primary care—or both.
The irony is that many people pass on coverage due to perceived cost, when in fact it’s far less expensive that most people think. The 2016 Insurance Barometer Study, by Life Happens and LIMRA showed that 8 in 10 people overestimate the cost of life insurance. For instance, a healthy, 30-year-old man can purchase a 20-year, $250,000 term life insurance policy for $160 a year—about $13 a month.
Enjoy the Benefits of Life Insurance—While You’re Alive
If budget pressures aren’t an issue, consider the living benefits of permanent life insurance—that’s right, benefits you can use during your own lifetime.
Permanent life insurance policies typically have a higher premium than term life insurance policies in the early years. But unlike term insurance, it provides lifelong protection and the ability to accumulate cash value on a tax-deferred basis.
Cash values can be used in the future for any purpose you wish. If you like, you can borrow cash value for a down payment on a home, to help pay for your children’s education or to provide income for your retirement.
When you borrow money from a permanent insurance policy, you’re using the policy’s cash value as collateral and the borrowing rates tend to be relatively low. And unlike loans from most financial institutions, the loan is not dependent on credit checks or other restrictions. You ultimately must repay any loan with interest or your beneficiaries will receive a reduced death benefit and cash-surrender value.
In this way, life insurance can serve as a powerful financial cushion for you and your family throughout your life, in addition to protecting your family from day one.
Disability Insurance: For the Biggest Risk of All
The most overlooked of the major types of insurance coverage is the one that actually covers a far more common risk—the risk of becoming ill or injured and being unable to work and earn your paycheck.
How common is it? While no one knows the exact numbers, it’s estimated that 30% of American workers will become disabled for 90 days or more during their working years. The sad reality is that most American workers also cannot afford such an event. In fact, illness and injury are the top reasons for foreclosures and bankruptcies in the U.S. today. Disability insurance ensures that if you are unable to work because of illness or injury, you will continue to receive an income and make ends meet until you’re able to return to work.
It’s tempting to cross your fingers and hope misfortune skips over you. But when you look at the facts, it’s easy to see: getting proper coverage against life’s risks is not just important, but a bargain in disguise.
See the original article Here.
Source:
Nataren E. (2017 May 11). The risk of being uninsured (and the hidden bargain in addressing it now) [Web blog post]. Retrieved from address https://www.lifehappens.org/blog/the-risk-of-being-uninsured-and-the-hidden-bargain-in-addressing-it-now/
Helping Your Employees Protect Against Identity Theft
Are you doing enough to help your employees protect themselves from identity theft? Make sure to take a look at this article by Irene Saccoccio from SHRM on what employers can do to protect their employees from identity theft.
Social Security is committed to securing today and tomorrow for you and your employees. Protecting your identity and information is important to us. Security is part of our name and we take that seriously.
Identity theft is when someone steals your personally identifiable information (PII) and pretends to be you. It happens to millions of Americans every year. Once identity thieves have your personal information they can open bank or credit card accounts, file taxes, or make new purchases in your name. You can help prevent identity theft by:
- Securing your Social Security card and not carrying it in your wallet;
- Not responding to unsolicited requests for personal information (your name, birthdate, social security number, or bank account number) by phone, mail, or online;
- Shredding mail containing PII instead of throwing it in the trash; and
- Reviewing your receipts. Promptly compare receipts with account statements. Watch for unauthorized transactions.
It is important that your employees take the necessary steps to protect their Social Security number. Usually, just knowing the number is enough, so it is important not to carry your Social Security card or other documents unless they are needed for a specific purpose. If someone asks for your employees’ number, they should ask why, how it will be used, and what will happen if they refuse. When hired, your employees should provide you with the correct Social Security number to ensure their records and tax information are accurate.
If your employees suspect someone else is using their Social Security number, they should visit IdentityTheft.gov to report identity theft and get a recovery plan. IdentityTheft.gov guides them through every step of the recovery process. It’s a one-stop resource managed by the Federal Trade Commission, the nation’s consumer protection agency. You can also call 1-877-IDTHEFT (1-877-438-4338); TTY 1-866-653-4261.
Your employee should also contact the Internal Revenue Service (IRS), and file an online complaint with the Internet Crime Complaint Center at www.ic3.gov.
Don’t let your employees fall victim to identity theft. Advise them to read our publication Identity Theft and Your Social Security Number or read our Frequently Asked Questions for more information. If you or an employee suspects that they’re a victim of identity theft, don’t wait, report it right away!
See the original article Here.
Source:
Saccoccio I. (2017 May ). Helping your employees protect against identity theft [Web blog post]. Retrieved from address https://blog.shrm.org/blog/helping-your-employees-protect-against-identity-theft